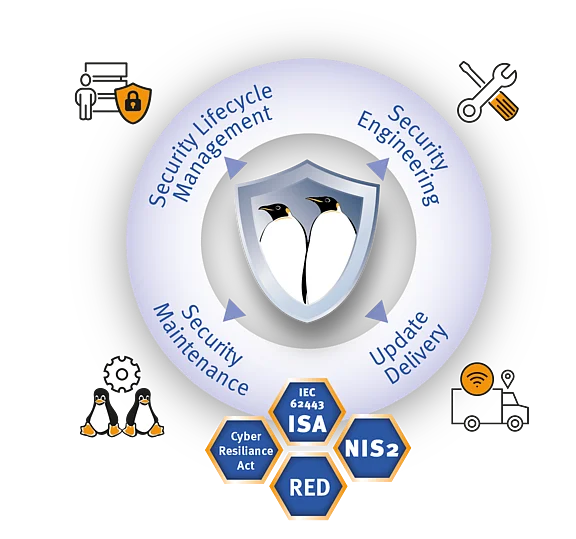
The Cyber Resilience Act (CRA) and the Radio Equipment Directive (RED) have introduced new compliance requirements that manufacturers must follow. To meet essential regulations such as IEC 62443, the BSI TR-03185-2 and the EN 18031, manufacturers are required to adhere to specific mandatory standards for cybersecurity and maintenance.
emlix Security Engineering
We offer security solutions specifically tailored to meet the needs of your product and its use cases. Our focus is mainly the operating system level with its interfaces to the hardware, the application level and backend services.
Our services include:
- Security-by-design concept development: software architecture, software requirements specification, assurance case
- Implementation of security measures e.g.:
- Hardened embedded Linux platform
- Secure boot & trusted boot
- Secure update concept, rollback mechanisms and recovery system
- Roles & rights management
- Logging and reporting on operating system level
- Secure communication
- Security and IP-protection in static and dynamic mode
- Set-up of a curated build toolchain, reliable version management
- Our toolchains facilitate: regulatory compliance documentation, reproducible builds,
automated testing and OSS compliance (SBOM, License Management) - Support with assessments
emlix CVE and lifecycle management for embedded Linux
To fulfill CRA and RED compliance requirements for embedded software lifecycle management, emlix provides CVE security management tools and services that maintain a secure, stable, and compliant Linux platform over the entire product lifecycle.
BEST PRACTICE
Rademacher Geräte-Elektronik GmbH
Increased cyber security through maintainability
In the development of the HomePilots® emlix was responsible for the conception of an embedded Linux-based platform.
The focus of the project was on the high security demands, because the intelligent devices transmit personal data such as camera material to the control unit. Furthermore, emlix is supporting Rademacher in maintaining the IT security of the product throughout its entire life cycle.