Embedded Linux in safety-critical contexts is extremely attractive. It removes the vendor lock-in of proprietary alternatives and offers the prospect of a significantly broader portfolio of technical and functional options.
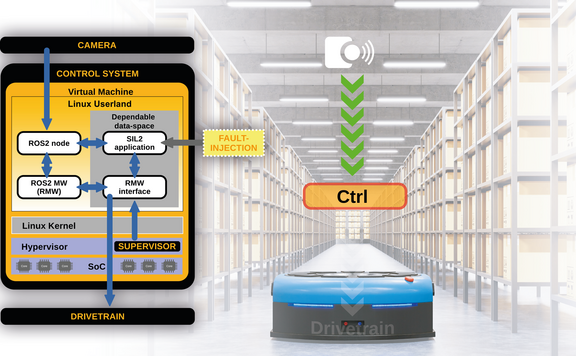
In March 2024, a completely new solution has received a positive and very far-reaching assessment from TÜV Nord. This applies to both IEC 61508 (SIL2) and ISO 26262 (ASIL B, SEooC): As part of an innovative development project together with Elektrobit Automotive GmbH in Erlangen, emlix has developed a Linux Safety Monitor which reliably supervises the Linux kernel, enabling a SIL2 application to be run directly on Linux. This allows bridging the gap between safety and open source solutions which has existed until now.
This solution is now available for project integrations in areas such as medical technology, industrial automation and power engineering.
Our embedded Linux and safety experts will be happy to discuss suitable architectures with you.
SIL2 Safety applications directly on Linux
Embedded Linux has been in use in various safety-critical applications for years. However, it is ordinarily reserved for non-safety-critical functions, most commonly communication, networking, update-functionality, and visualisation.
If a safety load is placed on the Linux system, a redundancy approach is predominantly used. This redundancy approach creates costs, both direct, such as for hardware, as well as indirect, for example for maintenance. As a rule, two different operating systems with two separate maintenance lifecycles will run on the two separate SOCs. The maintenance also requires the corresponding experties in both operating systems as well as communication at the interfaces.
This new architecture allows using high performance cores to run safety and QM applications in a Linux VM on a L4 based hypervisor.
Running rust, C, and C++ applications directly on the Linux system is no longer a problem with the Linux Safety Monitor and corresponding safety compiler. Further programming languages and compilers can also be used as long as they produce Linux-compatible ELF binaries.
Alongside the usual communication channels, a shared memory interface enables low latency communication, which safety applications can use to interact with each other. Futhermore, there exists a similar interface to a non-safety virtual machine available to safety applications.
Linux for Safety Applications in various industries
The approval against the requirements of both ISO26262 and IEC61508 massively expands the range of deployment possibilities in various industries.
In the industrial automation domain an example would be certain aspects of the control of safety-critical lasers. The configuration of the lasers could still be carried out by a non-safety-critical application. A safety-critical application would then ensure that the values never lie outside certain hard upper and lower limits. For example, these could be the intensity of the laser beam or the maximum angle of the orientation.
Another example, this time from the medical technology domain, demonstrates the potential of a Linux system supervised by the Linux Safety Monitor: displaying safety-critical information on the same screen as non-safety-critical information. A concrete example would be the vital signs of a patient together with alarm functionality, both of which must be entirely reliable, paired with some convenient information for the medical personal.
The display of safety-critical information cannot be corrupted by non-safety-critical data because the rendering happens in a separate layer that can never be overwritten. Critical data is then only rendered once a final check by the safety-related application has occurred.
These two examples show how the software architecture can be reimagined. Hardware costs will be reduced, although the real leverage lies in the massively reduced complexity of the lifecycle maintenance.
Through the integration of non-safety-critical and safety-critical applications on a single SOC it becomes possible to implement lower latency communication between the applications as well as to use the inherent performance of a Linux system.
Integrated Systems-, Safety-, and Security engineering
Based on cross-domain experience we gathered the last 25 years, we can offer to our customers our contribution to solutions in highly regulated context, especially with a strong focus on functional safety and cybersecurity. Integrating systems-, safety- and cyberscurity engineering ist the foundation for an effective overall design, that balances its design based on supportive but also contradicting requirements on a sound basis. The background at emlix paired with the ability to bring in expertise on functional safety and cybersecurity help, to find proper solutions on different levels of abstraction within architecture and design.
Finding a solution based on assessed building blocks with customer specific adaptations (EN 61508, ISO26262): Based on Linux for safety applications (ref 1, ref 2) and its design for long-term maintainability, we develop safe- and secure solutions based on embedded Linux and specific to our customers’ products
- for and with our customers.
- For use in highly regulated context – functional safety and cybersecurity
Engineering along the product life cycle as defined in standards and regulations: Our team does follow the life-cycle model as defined in standards and regulations and aligned with our customers. We support and contribute from the very beginning starting with concept development and along all phases, such as analysis, requirements engineering, architecture and design, implementation, integration and test.
Exemplary services are:
- Feasibility and preliminary studies
- Development of technical concepts based on requirements on functional safety and cybersecurity
- Support for analysis on safety and cybersecurity
- Requirements identification, development, analysis and selection
- Architecting and design
- Software development, selection and evaluation of open source technologies and configuration
- Qualification of Software of unknown provenance
- Creation of project sketches and realization plans
Success Story: Elektrobit - Linux for Safe Applications
In April 2024 a completely new approach to run SIL2 safety applications directly on a Linux system has been presented to the public: Elektrobit’s EB corbos Linux for safety applications (EbcLfSA) is the first OS-solution assessed by TÜV Nord to be compliant with safety standards up to SIL2/ASILB and based on embedded Linux. It is suitable for use in ISO 26262 as well as IEC 61508 projects as it can perform safety functions up to SIL2/ ASILB.